10 Nov 2013
How to make a basic blog: For Sangeeta Ma'am
06:39
No comments
STEP 1:
Go to http://www.blogger.com/start .
It will ask you for your google account username and password, login with the right credentials.
STEP 2:
Click on 'New Blog' Button:
Then give the title of the blog and Address, which will be used to access the blog. suppose you enter 'childrenbooks' then your blog's address will be http://childrenbooks.blogspot.com.
STEP 3:
Select the template you want from the list ( you can change it later). For example I have selected most basic template 'simple' from the list.
STEP 4:
After you click on 'Create Blog', a list will appear with the newly created blog name and your previous blogs(if you have any).
Click on the name of your blog on that list. It will take you to a window something like this:
Click on 'New Post'. Enter your post title and start writing the article, this will create your posts.
STEP 5:
Now go to 'Layout' in the left menu bar.
There you can easily edit your blog basic template like Header, Menu Bar ( in this case, right side vertical menu), also you can add multiple gadgets from available gadget list.:
If you want to change your template, go to Template option,
To add a custom domain to your blog, go to settings>Basics>Add a Custom Domain.
PAGES:
You can add multiple pages to add more functionality to your blog, for that:
in the left menu, go to pages,
You can see I have created a new page by clicking on the link 'New Page' just above the pages list.
By default visibility is 'Don't Show', you have to change it to 'Top Tabs' or 'Side Links' to show it on the blog.
I have selected top tabs:
11 Apr 2013
Hcon - Innovating Security
Hey all in this tutorial i will be telling you all about Hcon family as in my last post i told about the new tool made by Hcon family, so i thought to tell you all about Hcon and their intentions and the way of working.
You all must have thought that what does Hcon stands for, right ?? Well i also don't know but it was named by the founder and owner MR.Ashish Mistry. His main aim behind this was to give more and more knowledge to all of us. According to him certificate or degree's dosent matter but what matter is skills.
This provides us very easy and light interface tools whch can be easily understood and used. Their main aim is to help people know that how all this works instead of just making tools and let people use them.
They have their own platform and technique of working along with that they also give each and every of us to interfare and let them know what new we want and also inform about their mistakes or bugs.
Hcon has its own OS which is not available for everyone as it has some privacy so it is only available for the students of Hcon but hope so it will be soon available for public too.
As the news came after finishing the HconSTF linux x64 binary they are planning for some new projects and also new tutorials. Also soon Hcon will be launching some magazines which will be very useful for the people interested in getting updates and about new things.
You can get all the information and updates on the Hcon website and Hcon facebook page.
Website--> http://www.hcon.in
Facebook Page--> https://www.facebook.com/hcon.in
If anyone is interested in joining or contributing Hcon family in any way then he/she may contact the founder and owner through the website or page and may show his/her skills.
As the way they work and the output they give they seems to have a bright future they work for gaining and giving knowledge. Their aim is to learn and teach and share knowledge far and far.
Hope you all enjoyed this tutorial and if you have any problem or question then you may ask in comments.

What Is Hcon ?
You all must have thought that what does Hcon stands for, right ?? Well i also don't know but it was named by the founder and owner MR.Ashish Mistry. His main aim behind this was to give more and more knowledge to all of us. According to him certificate or degree's dosent matter but what matter is skills.
Features of Hcon
This provides us very easy and light interface tools whch can be easily understood and used. Their main aim is to help people know that how all this works instead of just making tools and let people use them.
They have their own platform and technique of working along with that they also give each and every of us to interfare and let them know what new we want and also inform about their mistakes or bugs.
Hcon has its own OS which is not available for everyone as it has some privacy so it is only available for the students of Hcon but hope so it will be soon available for public too.
More to Come
As the news came after finishing the HconSTF linux x64 binary they are planning for some new projects and also new tutorials. Also soon Hcon will be launching some magazines which will be very useful for the people interested in getting updates and about new things.
You can get all the information and updates on the Hcon website and Hcon facebook page.
Website--> http://www.hcon.in
Facebook Page--> https://www.facebook.com/hcon.in
If anyone is interested in joining or contributing Hcon family in any way then he/she may contact the founder and owner through the website or page and may show his/her skills.
As the way they work and the output they give they seems to have a bright future they work for gaining and giving knowledge. Their aim is to learn and teach and share knowledge far and far.
Hope you all enjoyed this tutorial and if you have any problem or question then you may ask in comments.
Hcon Security Testing Framework - v0.5 codename 'Prime' Released worldwide
Hey all its smarty out here sorry for not posting for too many days as i was busy in studies and other works, but i am again back with some really good stuffs.Hope you likeit
So, today i will be telling you all about a tool made by Hcon family whose owner MR. Ashish Mistry worked very hard for this.
You all might have heard about different security testing browsers,s/w etc. This is also security testing framework but i am telling it is very easy and comaptible than others.
It is fully customizable,easy to use,small in size and light on resources.
It contains hundreds of features for doing :
Web Penetration Testing
Web Exploits Development
Web Malware Analysis
OSINT & Cyber spying
1. Good and updated exploitation tools which can be easily used with security approaches also supports supports verbose debugging features for Web Exploit Development.

2. HconSTF contains blend of online and offline tools for Pentesting called 'WebUI' which includes encoders,scanners and many more things.

3. It also contains IDB which is an Integrated database with huge amount of Web payloads like :
Xss
Sqli
LDAP
Command execution

4. One of the bestest feature that is Osint available which helps in many Open source intelligence based tasks like :
Passive Web & Network Reconnaissance
Doxing
Cyber Spying
Hash cracking
It contains more than 165 plugins.

5. Encoding / Decoding & hashing Features and tools, supports wide variety of formats, character set and algorithms for making payloads undetectable.

6. It contains one of the best tools available for proxy and anonymizing networks.
Configured by :
Tor
AdvOR
I2P
Https, Socks 4 / 5

7. It also contains many integrated features for reporting things like :
Screenshots
Note taking
Session saving & exporting
Custom Url Logging
Automated Request logging

8. It is also hacker friendly because it i ncludes Hackery-Hybrid, collection of huge amount of learning bookmarks for learning any techniques, tools.

So, today i will be telling you all about a tool made by Hcon family whose owner MR. Ashish Mistry worked very hard for this.
You all might have heard about different security testing browsers,s/w etc. This is also security testing framework but i am telling it is very easy and comaptible than others.
Introduction
It is fully customizable,easy to use,small in size and light on resources.
It contains hundreds of features for doing :
Web Penetration Testing
Web Exploits Development
Web Malware Analysis
OSINT & Cyber spying
Features
1. Good and updated exploitation tools which can be easily used with security approaches also supports supports verbose debugging features for Web Exploit Development.

2. HconSTF contains blend of online and offline tools for Pentesting called 'WebUI' which includes encoders,scanners and many more things.

3. It also contains IDB which is an Integrated database with huge amount of Web payloads like :
Xss
Sqli
LDAP
Command execution

4. One of the bestest feature that is Osint available which helps in many Open source intelligence based tasks like :
Passive Web & Network Reconnaissance
Doxing
Cyber Spying
Hash cracking
It contains more than 165 plugins.

5. Encoding / Decoding & hashing Features and tools, supports wide variety of formats, character set and algorithms for making payloads undetectable.

6. It contains one of the best tools available for proxy and anonymizing networks.
Configured by :
Tor
AdvOR
I2P
Https, Socks 4 / 5

7. It also contains many integrated features for reporting things like :
Screenshots
Note taking
Session saving & exporting
Custom Url Logging
Automated Request logging

8. It is also hacker friendly because it i ncludes Hackery-Hybrid, collection of huge amount of learning bookmarks for learning any techniques, tools.

Other Features
- Available for both all Windows and Linux based systems
- Easy to use & collaborative Operating System like interface
- Includes Custom scripts for doing many pentesting tasks
- Includes Cleaner for running HconSTF smoothly
- Light on Hardware Resources & Small in size
- Portable - no need to install, can work from any USB storage device
- Multi-Language support (Partial)
- Works side-by-side with your normal web browser without any conflict issues
- Works on both architectures x86 & x64 on windows XP, Vista, 7 and on Linux with Wine
- Netbook compatible - User interface is designed for using framework on small screen sizes
- Free & Open source and always will be
Categories of Tools
- Recon / Mapping
- Editor / Debuggers
- Exploitation / Audit
- Anonymity
- Passwords
- Cryptography
- Database
- Scripting / Automation
- Network Utilities
- Reporting
Download link --> http://www.hcon.in/downloads.html
For more details go to http://www.hcon.in/
Hope you all enjoyed this tutorial and if you have any problem or question then you may ask in comments.
21 Mar 2013
Metasploit Live Webcam Streaming Of Victim
Its me Aitezaz Known as Soldier Of God (SOG)
You all will be enjoying ur good days !
This Tut is About Webcam hacking !
So when You are successful in compromising a Remote system and after meterpreter session is opened , how to Watch Live Streaming Ov Victim Webcam.
Video Link = http://www.youtube.com/watch?v=17RXTGacKes
4 Dec 2012
Introducing Practical Computer Networks: From a Hacker's Prospective Discussion 1
06:04
computer networks, Kumar Sourav, network hacking, penetration testing, Practical Computer Networks, pwnscar
No comments
How you been ? Its been a long time since i made any post . :) Missed me ? (kidding ).
So I said i will be making a new series of video discussions titled " Practical Computer Networks: From a Hacker's Prospective", here i am publishing first video of the series.
Well you must be knowing how much important computer networks are if you want to go for hacking or cyber security. So i thought i would help you as much as i can by providing whatever i know. Computer Network is my favorite subject.
I wrote "From a hacker's prospective". What does that mean? actually i am trying to make it more hacking oriented thats why :)
so have fun. Thanks for all your support !
1 Dec 2012
Penetration Testing with iPhone Applications - Part 3
In third part we will make an in-depth analysis on the keychain data storage, understanding of the keychain and its security and also its weakness will help penetration testers for further attacks.
Keychain is an encrypted container (128 bit AES algorithm) and a centralized SQLite database that holds identities & passwords for multiple applications and network services, with restricted access rights. On the iPhone, keychain SQLite database is used to store the small amounts of sensitive data like usernames, passwords, encryption keys, certificates and private keys.
iOS applications use the keychain service library/API (secItemAdd, secItemDelete, secItemCopyMatching & secItemUpdate methods) to read and write data to and from the keychain. Developers leverage the keychain services API to dictate the operating system to store sensitive data securely on their behalf, instead of storing them in a property list file or a plaintext configuration file. On the iPhone, the keychain SQLite database file is located at – /private/var/Keychains/keychain-2.db.
Keychain contains a number of keychain items and each keychain item will have encrypted data and a set of unencrypted attributes that describes it. Attributes associated with a keychain item depend on the keychain item class (kSecClass). In iOS, keychain items are classified into 5 classes – generic passwords (kSecClassGenericPassword), internet passwords (kSecClassInternetPassword), certificates (kSecClassCertificate), keys (kSecClassKey) and digital identities (kSecClassIdentity, identity=certificate + key). In the iOS keychain, all the keychain items are stored in 4 tables – genp, inet, cert and keys. Genp table contains generic password keychain items, inet table contains Internet password keychain items, and cert & keys tables contain certificates, keys and digital identity keychain items.
Columns in the keychain tables are mapped to the corresponding keychain item class attributes.
genp table columns shown in below image are mapped to Generic password keychain item class attributes as shown in Table 1.

(Figure 1)
Table 1
Attributes for all the keychain item classes are documented in the Keychain Item class keys and Values section in Apple’s documentation.The keychain database is encrypted with a hardware-specific key which is unique per the device. The hardware key cannot be extracted from the device, so the data stored in the keychain can only be accessible on the device itself and cannot be moved to another device. The keychain database is tied to the device, so even if an attacker obtains access to the keychain through physical access to the file system or in a remote attack, he cannot decrypt and view the file contents. The keychain file format is shown in Table 2.
(Table 2)
Keychain data is logically zoned and data stored by one application is not accessible to another application. Keychain data of an iOS application is stored outside the application’s sandbox. So the operating system process securityd enforces the access control and regulates access to the keychain data in such a way that the applications with correct permissions can read their data. Keychain access permissions of an iOS application are defined in the code sign entitlements. Keychain Services uses these entitlements to grant permissions for the applications to access its own keychain items.
Entitlements of an application define the properties that provide access to the iOS features such as push notifications, keychain access and iCloud communication, etc… Entitlements grant specific capabilities or security permissions to iOS applications. An entitlement file for a keychain data sharing application contains an application-identifier and may contain a set of keychain-access-groups constants. In iOS, each application ships with a unique application-identifier. The keychain service restricts the keychain data access based on this application identifier. By default, applications can only access data associated with their own application-identifier.
Later, to share the keychain items with multiple applications, keychain-access-groups were introduced. Applications with the same keychain access group entitlement can access/share the keychain items. Entitlements of an application are embedded in the application binary and stored unencrypted. So, on a JailBroken iPhone, entitlements of an application can be extracted from the application binary using grep or sed commands (stream editor – sed can be downloaded from Cydia packages).
To list out the entitlements of an iOS application, connect to the iPhone over SSH, navigate to the application’s home directory (/var/mobile/Applications/[unique-id]/) and run the below command.
[CODE]
sed -n ‘//,/<\/dict>/p’ [AppDirectory]/[ApplicationBinary]
[/CODE]
For example below command will list out the entitlements of Facebook iOS application.
[CODE]
> sed -n ‘//,/<\/dict>/p’ Facebook.app/Facebook application-identifier T84QZS65DQ.com.facebook.Facebook aps-environment production keychain-access-groups T84QZS65DQ.platformFamily
[/CODE]
Facebook iOS application is a fat binary (built for ARM6 & ARM7 architectures), so the above command will print the entitlement details twice.
The above result shows that the Facebook iOS application uses ‘T84QZS65DQ.platformFamily’ keychain-access-group while storing the entries in the keychain.
When an application adds an entry to the keychain, an application identifier or keychain access group of the application also gets added to the keychain item agrp (access group) column. Later, when an application tries to access the keychain item, the keychain service verifies the application identifier or keychain access group against the agrp value of corresponding keychain item to permit the access. A sample keychain-2.db file is shown in Figure 3 and Facebook entitlements are highlighted.

(Figure2)
Note--> Applications that are built for the simulator use the same default keychain access group. So on the simulator, all the applications can access all the keychain items.
With the introduction of data protection mechanisms in iOS, sensitive data stored in the keychain item is protected with another layer of encryption which is tied to the user’s passcode. Data protection encryption keys (protection class keys) are derived from a device’s hardware key and a key generated from the user’s passcode. So encryption offered by data protection API is as good as the strength of a user’s passcode. Data protection is designed to protect the user’s data in case a device is lost or stolen. Data protection for the keychain items can be enabled by supplying an accessibility constant value to the kSecAttrAccessible attribute of SecItemAdd or SecItemUpdate methods.
Data protection accessibility constants determine when a keychain item should be readable by an application. They also determine whether a keychain item is allowed to migrate to other devices or not. During an iTunes backup, all the data stored in the iOS device is backed up to the computer including the keychain database. On the iTunes backups, the keychain SQLite database is stored as a Plist file (Keychain-backup.plist). Keychain items which are backed-up with the iTunes encrypted backup option can be moved/loaded to another device. However the keychain items which are protected with ThisDeviceOnly constants cannot be moved to other iOS devices.
Below is the list of keychain item accessibility constants –
(Table 3)
Keychain Storage
Keychain is an encrypted container (128 bit AES algorithm) and a centralized SQLite database that holds identities & passwords for multiple applications and network services, with restricted access rights. On the iPhone, keychain SQLite database is used to store the small amounts of sensitive data like usernames, passwords, encryption keys, certificates and private keys.
iOS applications use the keychain service library/API (secItemAdd, secItemDelete, secItemCopyMatching & secItemUpdate methods) to read and write data to and from the keychain. Developers leverage the keychain services API to dictate the operating system to store sensitive data securely on their behalf, instead of storing them in a property list file or a plaintext configuration file. On the iPhone, the keychain SQLite database file is located at – /private/var/Keychains/keychain-2.db.
Keychain contains a number of keychain items and each keychain item will have encrypted data and a set of unencrypted attributes that describes it. Attributes associated with a keychain item depend on the keychain item class (kSecClass). In iOS, keychain items are classified into 5 classes – generic passwords (kSecClassGenericPassword), internet passwords (kSecClassInternetPassword), certificates (kSecClassCertificate), keys (kSecClassKey) and digital identities (kSecClassIdentity, identity=certificate + key). In the iOS keychain, all the keychain items are stored in 4 tables – genp, inet, cert and keys. Genp table contains generic password keychain items, inet table contains Internet password keychain items, and cert & keys tables contain certificates, keys and digital identity keychain items.
Columns in the keychain tables are mapped to the corresponding keychain item class attributes.
genp table columns shown in below image are mapped to Generic password keychain item class attributes as shown in Table 1.

(Figure 1)
| column | Attribute | description |
| cdat | kSecAttrCreationDate | Item creation date in Unix epoch time format |
| mdat | kSecAttrModificationDate | Item modification date in Unix epoch time format |
| desc | kSecAttrDescription | User visible string that describes the item |
| icmt | kSecAttrComment | User editable comment for the item |
| crtr | kSecAttrCreator | Application created (4 char) code |
| type | kSecAttrType | Item type |
| scrp | kSecAttrScriptCode | String script code (such as encoding type) |
| labl | kSecAttrLabel | Label to be displayed to the user (print name) |
| alis | kSecAttrAlias | Item alias |
| invi | kSecAttrIsInvisible | Invisible |
| nega | kSecAttrIsNegative | Invalid item |
| cusi | kSecAttrHasCustomIcon | Existence of application specific icon (Boolean) |
| prot | kSecProtectedDataItemAttr ? | Item’s data is protected (Boolean) |
| acct | kSecAttrAccount | Account key (such as user id) |
| svce | kSecAttrService | Service name (such as Application identifier) |
| gena | kSecAttrGeneric | User defined attribute |
| data | kSecValueData |
Actual data (such as password, crypto key…) |
| agrp | kSecAttrAccessGroup | Keychain access group |
| pdmn | kSecAttrAccessible | Access restrictions (Data protection classes) |
Table 1
Attributes for all the keychain item classes are documented in the Keychain Item class keys and Values section in Apple’s documentation.The keychain database is encrypted with a hardware-specific key which is unique per the device. The hardware key cannot be extracted from the device, so the data stored in the keychain can only be accessible on the device itself and cannot be moved to another device. The keychain database is tied to the device, so even if an attacker obtains access to the keychain through physical access to the file system or in a remote attack, he cannot decrypt and view the file contents. The keychain file format is shown in Table 2.
| Version | Protection class | len_wrapped key | AESWRAP (class key, item key, len_wrapped key) | AES256_GCM(item key, data) | Integrity tag(16 bytes) |
Keychain data is logically zoned and data stored by one application is not accessible to another application. Keychain data of an iOS application is stored outside the application’s sandbox. So the operating system process securityd enforces the access control and regulates access to the keychain data in such a way that the applications with correct permissions can read their data. Keychain access permissions of an iOS application are defined in the code sign entitlements. Keychain Services uses these entitlements to grant permissions for the applications to access its own keychain items.
Entitlements of an application define the properties that provide access to the iOS features such as push notifications, keychain access and iCloud communication, etc… Entitlements grant specific capabilities or security permissions to iOS applications. An entitlement file for a keychain data sharing application contains an application-identifier and may contain a set of keychain-access-groups constants. In iOS, each application ships with a unique application-identifier. The keychain service restricts the keychain data access based on this application identifier. By default, applications can only access data associated with their own application-identifier.
Later, to share the keychain items with multiple applications, keychain-access-groups were introduced. Applications with the same keychain access group entitlement can access/share the keychain items. Entitlements of an application are embedded in the application binary and stored unencrypted. So, on a JailBroken iPhone, entitlements of an application can be extracted from the application binary using grep or sed commands (stream editor – sed can be downloaded from Cydia packages).
To list out the entitlements of an iOS application, connect to the iPhone over SSH, navigate to the application’s home directory (/var/mobile/Applications/[unique-id]/) and run the below command.
[CODE]
sed -n ‘//,/<\/dict>/p’ [AppDirectory]/[ApplicationBinary]
[/CODE]
For example below command will list out the entitlements of Facebook iOS application.
[CODE]
> sed -n ‘//,/<\/dict>/p’ Facebook.app/Facebook application-identifier T84QZS65DQ.com.facebook.Facebook aps-environment production keychain-access-groups T84QZS65DQ.platformFamily
[/CODE]
Facebook iOS application is a fat binary (built for ARM6 & ARM7 architectures), so the above command will print the entitlement details twice.
The above result shows that the Facebook iOS application uses ‘T84QZS65DQ.platformFamily’ keychain-access-group while storing the entries in the keychain.
When an application adds an entry to the keychain, an application identifier or keychain access group of the application also gets added to the keychain item agrp (access group) column. Later, when an application tries to access the keychain item, the keychain service verifies the application identifier or keychain access group against the agrp value of corresponding keychain item to permit the access. A sample keychain-2.db file is shown in Figure 3 and Facebook entitlements are highlighted.

(Figure2)
Note--> Applications that are built for the simulator use the same default keychain access group. So on the simulator, all the applications can access all the keychain items.
With the introduction of data protection mechanisms in iOS, sensitive data stored in the keychain item is protected with another layer of encryption which is tied to the user’s passcode. Data protection encryption keys (protection class keys) are derived from a device’s hardware key and a key generated from the user’s passcode. So encryption offered by data protection API is as good as the strength of a user’s passcode. Data protection is designed to protect the user’s data in case a device is lost or stolen. Data protection for the keychain items can be enabled by supplying an accessibility constant value to the kSecAttrAccessible attribute of SecItemAdd or SecItemUpdate methods.
Data protection accessibility constants determine when a keychain item should be readable by an application. They also determine whether a keychain item is allowed to migrate to other devices or not. During an iTunes backup, all the data stored in the iOS device is backed up to the computer including the keychain database. On the iTunes backups, the keychain SQLite database is stored as a Plist file (Keychain-backup.plist). Keychain items which are backed-up with the iTunes encrypted backup option can be moved/loaded to another device. However the keychain items which are protected with ThisDeviceOnly constants cannot be moved to other iOS devices.
Below is the list of keychain item accessibility constants –
- kSecAttrAccessibleWhenUnlocked
- Keychain item is accessible only after the device is unlocked
- Data protection class keys required to decrypt the keychain items are loaded into memory only when the device is unlocked and the encryption keys are automatically purged in 10 seconds once the device is locked.
- kSecAttrAccessibleAfterFirstUnlock
- Keychain item is accessible only after the first unlock of the device until reboot
- Data protection class keys required to decrypt the keychain items are loaded into memory only when the user unlocks the device after a reboot, and the keys remain in the memory til next reboot of the device.
- kSecAttrAccessibleAlways
- Keychain item is accessible even when the device is locked
- Data protection class keys required to decrypt the keychain items are always loaded into memory.
- kSecAttrAccessibleWhenUnlockedThisDeviceOnly
- Keychain item is accessible only after the device is unlocked, and the item cannot be migrated between devices.
- kSecAttrAccessibleAfterFirstUnlockThisDeviceOnly
- Keychain item is accessible after the first unlock of the device and the item cannot be migrated between devices.
- kSecAttrAccessibleAlwaysThisDeviceOnly
- Keychain item is accessible even when the device is locked and the item cannot be migrated between devices.
| pdmn | Keychain accessibility constants |
| ak | kSecAttrAccessibleWhenUnlocked |
| ck | kSecAttrAccessibleAfterFirstUnlock |
| dk | kSecAttrAccessibleAlways |
| aku | kSecAttrAccessibleWhenUnlockedThisDeviceOnly |
| cku | kSecAttrAccessibleAfterFirstUnlockThisDeviceOnly |
| dku | kSecAttrAccessibleAlwaysThisDeviceOnly |
(Table 3)
11 Nov 2012
Penetration Testing with iPhone Applications - Part 2
Privacy Issues
Every iPhone has an associated unique device Identifier derived from a set of hardware attributes called UDID. It is burned into the device and one cannot remove or change it. However, it can be spoofed with the help of tools like UDID Faker.
UDID of the latest iPhone is computed with the
formula given below -
UDID = SHA1(Serial Number + ECID + LOWERCASE
(WiFi Address) + LOWERCASE(Bluetooth Address))
UDID is exposed to application developers through
an API which would allow them to access the UDID of an iPhone without requiring
the device owner’s permission.
There's a
code snippet which is used to collect the UDID of a device, later which
can used to track the user’s behavior.
Code: NSString *uniqueIdentifier = [device
uniqueIdentifier]
It is known that with the help of UDID, it is
possible to observe the user’s browsing patterns and trace out the user’s geo
location. As it is possible to locate the user’s exact location with the help
of a device UDID, it became a big privacy concern.
Openfient collected device UDID’s and misused
them by linking it to real world user identities (like email address, geo
locations latitude & longitude, Facebook profile picture) and making them
available for public access, resulting in a serious privacy breach.
While penetration testing, observe the network
traffic for UDID transmission. UDID in the network traffic indicates that the
application is collecting the device identifier or might be sending it to a
third party analytic company to track the user’s behaviour. In iOS 5, Apple has
deprecated the API that gives access to the UDID, and it will probably remove
the API completely in future iOS releases. Development best practice is not to
use the API that collects the device UDIDs, as it breaches the privacy of the
user. If the developers want to keep track of the user’s behaviour, create a
unique identifier specific to the application instead of using UDID. The
disadvantage with the application specific identifier is that it only
identifies an installation instance of the application, and it does not
identify the device.
Apart from UDID, applications may transmit
personal identifiable information like age, name, address and location details
to third party analytic companies. Transmitting personal identifiable
information to third party companies without the user’s knowledge also violates
the user’s privacy. So, during penetration testing carefully observe the
network traffic for the transmission of any important data.
Example: Pandora application was used to transmit
user’s age and zip code to a third party analytic company (doubleclick.net) in
clear text. For the applications which require the user’s geo location (ex:
check-in services) to serve the content, it is always recommended to use the
least degree of accuracy necessary. This can be achieved with the help of
accuracy constants defined in core location framework (ex: CLLocationAccuracy
kCLLocationAccuracyNearestTenMeters).
Local data storage
Mobile applications store the data locally on the
device to maintain essential information across the application execution or
for a better performance or offline access. Also, developers use the local
device storage to store information such as user preferences and application
configurations. As device theft is becoming an increasing concern, especially
in the enterprise, insecure local storage is considered to be the top risk in
mobile application threats. A recent survey conducted by Viaforensics revealed
that 76 percent of mobile applications are storing user’s information on the
device. 10 percent of them are even storing the plain text passwords on the
phone.
A few ways from which data stored in iPhone can
be obtained by attacker's are:
From Backups
When an iPhone is connected to iTunes, iTunes
automatically takes a backup of everything on the device. Upon backup,
sensitive files will also end up on the workstation. So an attacker who gets
access to the workstation can read the sensitive information from the stored
backup files.
Physical access to the device
People lose their phones and phones get stolen
very easily. In both cases, an attacker will get physical access to the device
and read the sensitive information stored on the phone. The passcode set to the
device will not protect the information as it is possible to brute force the
iPhone simple passcode within 20-30 minutes.
Malware
Leveraging a security weakness in iOS may allow
an attacker to design a malware which can steal the files on the iPhone
remotely.
iPhone application directory structure
In iOS, applications are treated as a bundle
represented within a directory. The bundle groups all the application
resources, binaries and other related files into a directory. In iPhone,
applications are executed within a jailed environment (sandbox or seatbelt)
with mobile user privileges. Unlike Android UID based segregation, iOS
applications runs as one user. Each and almost every application has access to
the contents of its own sandbox but cannot access other applications’. When an
application is first installed on a device, the system creates the
application’s home directory, sets up some key subdirectories, and sets up the
security privileges for the sandbox“. A sandbox is a restricted environment
that prevents applications from accessing unauthorized resources; however, upon
iPhone JailBreak, sandbox protection gets disabled.
When an application is installed on the iPhone,
it creates a directory with a unique identifier under /var/mobile/Applications
directory. Everything that is required for an application to execute will be
contained in the created home directory. Typical iPhone application home
directory structure is listed below
In iPhone, information could be stored in any of the locations listed below :
1. Plist
files
2. Keychain
2. Keychain
3.
Application’s home directory
4. Cache
5.
Logs.
Property list files
Itis a structured binary formatted file which
contains the essential configuration of a bundle executable in nested key value
pairs. These files are used to store the user preferences and the configuration
information of an application. For example, Gaming applications usually store
game levels and game scores in the Plist files. In general, applications store
the Plist files under [Application's Home Directory]/documents/preferences
folder. Plist can either be in XML format or in binary format. As XML files are
not the most efficient means of storage, most of the applications use binary
formatted Plist files. Binary formatted data stored in the Plist files can be
easily viewed or modified using Plist editors (ex: plutil). Plist editors
convert the binary formatted data into an XML formatted data, later it can be
edited easily. Plist files are primarily designed to store the user preferences
& application configuration; however, the applications may use Plist files
to store clear text usernames, passwords and session related information. So,
while penetration testing, view all the Plist files available under application’s
home directory and look for sensitive information, like usernames, passwords,
user’s personal information and session cookies, etc… Developers can assign any
extension to the Plist files. A Plist file can be easily identified by looking
at the file contents using cat command. The content of a Plist file starts with
bplist’.
Along with the sensitive information storage,
application may also take authentication & authorization decisions based on
the values stored in Plist files. For example, if you notice a Plist entry like
admin=0 during penetration testing, change the admin key value to 1 and open
the application. If the application does not validate the user input properly
and takes the authorization decision based on the Plist entry, you may log into
the application as an administrator. Development best practice is to not store
any sensitive information in Plist files. Also, do not take authentication
& authorization decisions based on the information stored in Plist files.
Plist files contain user controlled input, and it should be validated properly
like any other user input.
WordPress iPhone application used to store clear
text username and password in a Plist file. The video below here demonstrates
the WordPress vulnerability. This vulnerability was reported by SANS and
WordPress fixed it immediately.
Plist can be viewed and modified in both
JailBroken and non JailBroken iPhones.Below are examples of both of them.
Tampering Plist files on a non JailBroken iPhone:
On a non JailBroken iPhone, Plist files can be
viewed & modified using tools like iExplorer and iBackupBot.
Modifying Plist entries with iExplorer
iExplorer (iPhone Explorer) gives access to the
iPhone in disk mode and allows browsing all the folders on the iPhone directly.
Stick Cricket iPhone game is used for the
example.
Stick Cricket iPhone game stores the game score
in a Plist file under application’s home directory. As the application is
storing the game score locally in a Plist file, it can be altered by editing
the Plist file.
Screenshot shown below displays the actual score
before the Plist modification.
Steps shown below will tellthe usage of iExplorer
tool to modify the game scores stored in the Plist file -
1. On your workstation download and install
iExplorer.
2. Connect the iPhone to the workstation over
USB.
3. In iExplorer, browse to Apps->com.sticksports.stickcricket
folder.
4. Navigate to stick cricket
Library->Preferences folder.
5. Copy com.sticksports.stickcricket.Plist file
to the workstation by dragging it to the desktop.
6. On the workstation, open the Plist file using
a Plist editor and modify the yourBest5Overs key value.


7. From iExplorer, delete the
com.sticksports.stickcricket.Plist on the iPhone and drag the newly saved file
onto the iPhone.
8. In iPhone, terminate the Stick Cricket
application and reopen it. The Stick Cricket welcome screen now displays the
modified score as shown in the screenshot below.

Modifying Plist entries with iBackupBot
When the iPhone is connected to a computer,
iTunes takes a backup of everything on the phone including configuration files
(Plist files). iBackupBot tool can be used to view and modify the Plist file
entries on the iPhone backup and restore the modified backup onto the iPhone..
Steps shown below will tell the use of iBackupBot
tool to modify the game scores stored in the Plist file -
1.
Connect
the iPhone to the workstation over USB cable.
2.
On
Workstation, open iTunes and take a backup of the iPhone.
3.
Close
iTunes.
4.
Open
iBackupBot. It automatically identifies the existing backups and displays the
files inside the backup to the user.
5.
Click
on Stick Cricket and open /Library/Preferences/com.sticksports.stickcricket.Plist
file.

6.
Modify
the score stored in the Plist file.
7.
Click
on Export icon to save the modified Plist file.
8.
Click
the restore icon in iBackupBot toolbar. It will restore the iPhone with the
modified backup. Now on iPhone, reopening the Stick Cricket game will display
the modified score.
Tampering Plist files on a JailBroken iPhone:
On a JailBroken iPhone, Plist files can be viewed
& modified using tools like plutil and iFile. Both these tools can be
downloaded from Cydia (packages – com.eric.tool & iFile). iFile would allow
to modify the Plist files directly on the iPhone.
The iPhone camera application is used for the
demo. In iOS camera application, Apple has hidden the panorama mode feature and
planned to include this feature in future iOS versions. Panorama mode basically
allows the users to take continuous photos while panning the camera from left
to right. Apple stored the panorama mode switch in a Plist file. iOS hackers
Conard & Chpwn exposed the panorama mode in iOS 5 by modifying an entry in
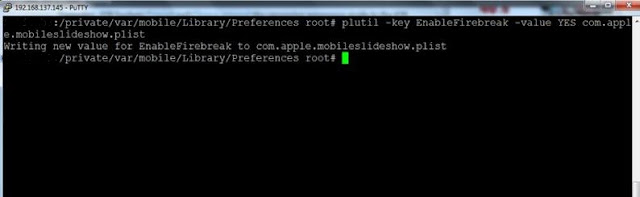
com.apple.mobileslideshow.Plist file.
Screenshot shown below displays the list of
options available in the iPhone camera application.

Steps shown below will tell the usage of plutil
tool to change the panorama switch stored in the Plist file -
1.
SSH
to the iPhone and login as a root user (password: alpine).
2.
Navigate
to /private/var/mobile/Library/Preferences/ directory.
3.
View
com.apple.mobileslideshow.Plist file content with the help of plutil
tool.
Plutil com.apple.mobileslideshow.plist
4.
Add
‘EnableFirebreak’ key to the com.apple.mobileslideshow.plist file with
the below command.
Plutil –key EnableFirebreak –value yes com.apple.mobileslideshow.plist
5.
It
turns on the panorama feature in the iPhone camera application.
Screenshot below shows different options available in
the iPhone camera after the modification

Hope you all enjoyed this tutorial and if you have any problem or question then you may ask in comments.
Subscribe to:
Posts (Atom)